Cyber Guardians of the Galaxies: Safeguarding Space Assets in the Digital Frontier
About Course
As humanity ventures deeper into space, our dependence on satellites and digital space infrastructure grows exponentially. From global communications and navigation to national defense and disaster monitoring, space assets are the silent sentinels of modern civilization. But with this rise comes an urgent threat — cyberattacks targeting the very core of our orbital operations. Cyber Guardians of the Galaxies invites students into the hidden realm of space cybersecurity, where high-stakes hacking, digital warfare, and futuristic defenses define a new digital frontier.
This course takes you on an immersive journey through the vulnerabilities of the New Space Age, revealing the anatomy of real space cyberattacks and the innovative strategies deployed to defend against them. Students will explore everything from the ground station defenses to tamper-proof satellite protocols, from quantum encryption to AI-powered threat detection. Whether you’re a tech enthusiast, aspiring cyber professional, or space policy student, you’ll discover how to become a digital guardian of the final frontier.
Course Content
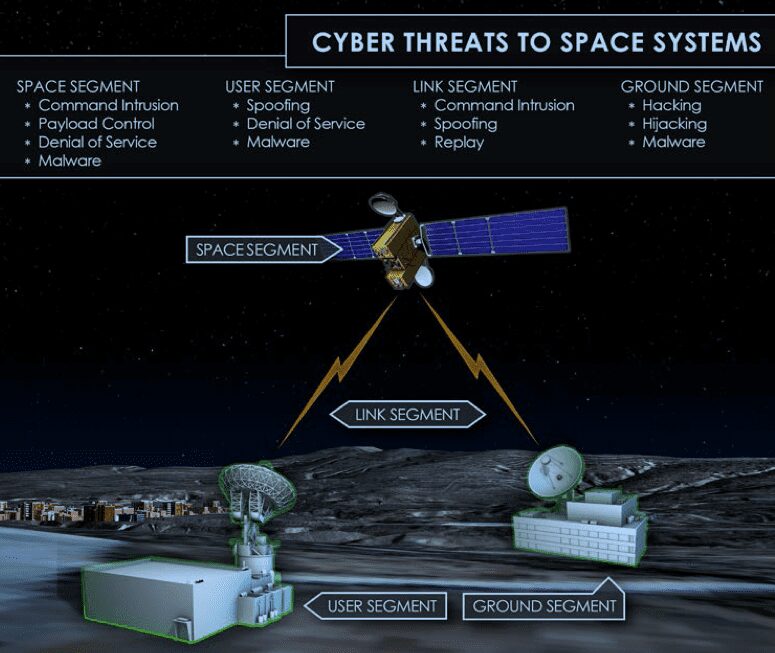
Chapter 1: The New Space Age and Its Vulnerabilities
The role of satellites and LEO constellations in modern society
00:00Growing cyber threats to space assets: motivations and potential consequences
00:00High-profile cyber incidents targeting space infrastructure
00:00