Deception Technology for Cyber Security: The Art of Misdirection
About Course
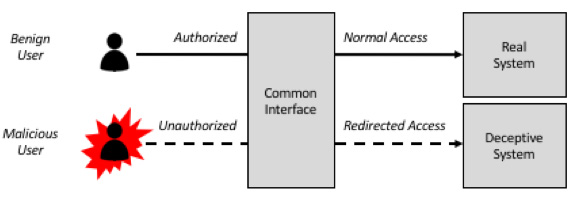
In the ever-evolving world of cybersecurity, traditional defense mechanisms are no longer enough to keep up with increasingly sophisticated threats. Enter Deception Technology—an innovative and strategic approach to cybersecurity that turns the tables on attackers by leading them down a path of illusions. This course, Deception Technology for Cybersecurity: The Art of Misdirection, introduces students to the fascinating world where traps, fake data, and emulated systems confuse and delay intruders, providing defenders with the upper hand.
Whether you’re a student of cybersecurity or an experienced IT professional, this course will take you through the theory and practice of using digital deception to detect, deflect, and counteract malicious intrusions. From honeypots and fake credentials to advanced deception networks and misleading metadata, you’ll explore how organizations deploy these tools to lure attackers into revealing themselves. With real-world case studies and simulations, you’ll not only learn the “what” and “why” of deception but also the “how”—preparing you to think like an attacker and defend like a strategist.
Course Content
Introdution
Definition of deception technology for security
00:00Importance of deception technology in modern cybersecurity
00:00