Encryption Technologies: Securing Your Data at Rest and in Transit
Course Content
Introduction
-
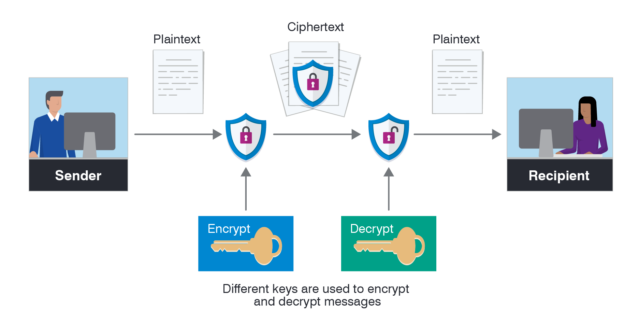
Explanation of encryption technologies
00:00 -
Importance of securing data
00:00 -
Overview of topics to be covered
00:00