Mastering Cybersecurity: A Comprehensive Guide to Vulnerability Assessment and Mitigation
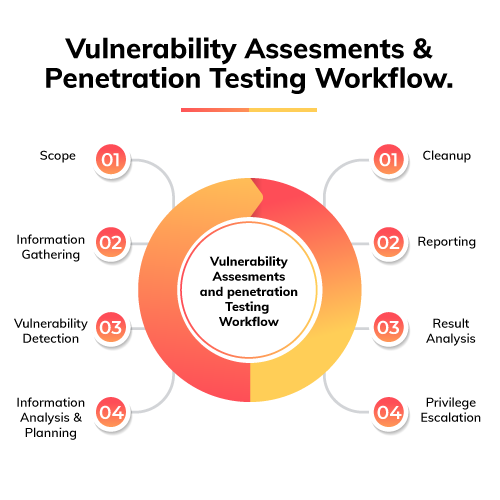
About Course
In an era where cyber threats are evolving at an unprecedented pace, mastering cybersecurity is no longer optional—it’s essential. Cyber vulnerabilities can emerge from software loopholes, hardware flaws, or even human error, making organizations and individuals vulnerable to devastating attacks. From ransomware and zero-day exploits to social engineering and insider threats, attackers continuously adapt their tactics, requiring cybersecurity professionals to stay ahead of the curve.
This course provides a comprehensive, hands-on approach to identifying, assessing, and mitigating cyber vulnerabilities. Whether you’re a security analyst, IT professional, or ethical hacker, you’ll gain invaluable insights into the latest vulnerability assessment techniques, mitigation strategies, and cutting-edge tools, including AI-driven threat detection. By the end of this course, you’ll be equipped with the knowledge and skills to safeguard networks, systems, and data against even the most sophisticated cyber threats.
Course Content
Introduction
The Increasing Importance of Cybersecurity
00:00The Ever-Present Threat of Cyber Vulnerabilities
00:00The Need for a Comprehensive Approach to Vulnerability Assessment and Mitigation
00:00