Mobile Device Security: Securing the Weakest Link
About Course
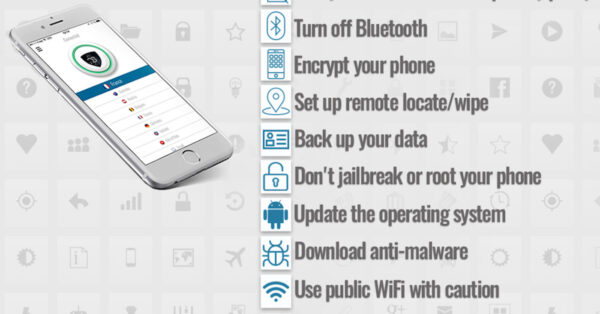
In today’s hyper-connected world, mobile devices have become the backbone of both personal and professional life—but they are also one of the most vulnerable entry points for cyber threats. Mobile Device Security: Securing the Weakest Link is an engaging and practical course designed to educate you on the growing risks posed to mobile platforms and how to effectively secure them. From malware and phishing scams to social engineering and public Wi-Fi risks, this course dives deep into the ever-evolving landscape of mobile security threats.
Whether you’re an IT professional, business leader, student, or simply someone who values digital privacy, this course equips you with the knowledge to defend against attacks, prevent data loss, and implement strong mobile security practices. Through real-world case studies, best practice checklists, and future-facing strategies, you will not only learn how to safeguard devices today but also anticipate the threats of tomorrow.
Course Content
Introduction
Definition of Mobile Device Security
00:00Importance of Mobile Device Security
00:00Purpose of the eBook
00:00