Next-Generation Firewall Technology: Protecting Networks from Advanced Threats
About Course
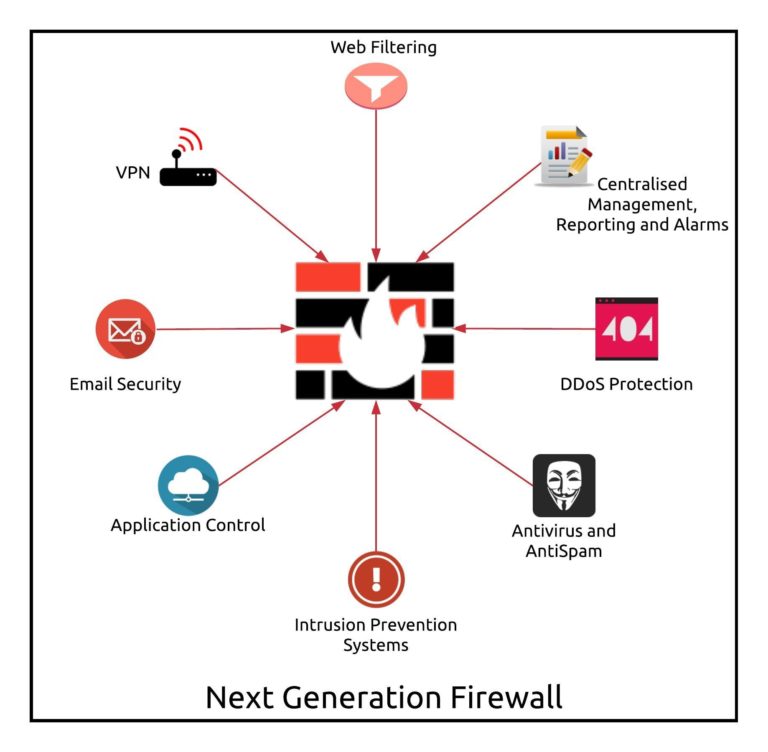
In today’s rapidly evolving digital landscape, networks are increasingly vulnerable to sophisticated cyber threats. Traditional firewalls, while effective in the past, no longer provide the robust protection needed against modern, advanced attacks. This course delves into Next-Generation Firewall (NGFW) technology, which integrates advanced features like application awareness, intrusion prevention, and threat intelligence to offer superior protection. Through this course, students will explore the key components of NGFWs and understand how they provide comprehensive defense against malware, ransomware, APTs, and other advanced persistent threats. By the end, you will gain a strong understanding of how to deploy and manage NGFWs to secure your network against increasingly complex attacks.
The course also looks forward, offering insights into the future of NGFW technology. With the integration of machine learning and artificial intelligence, firewalls are evolving to detect and prevent threats more effectively. This is not just about learning to configure firewalls—it’s about understanding how to future-proof your security infrastructure. Whether you’re a network administrator, security professional, or an IT manager, this course will equip you with the knowledge to safeguard your network against advanced threats and keep your data secure.
Course Content
Introduction
Definition of Next-Generation Firewall Technology
00:00Importance of advanced threat protection in network security
00:00