Quantum Key Distribution (QKD) Technology: Advancements, Applications and Market Trends
About Course
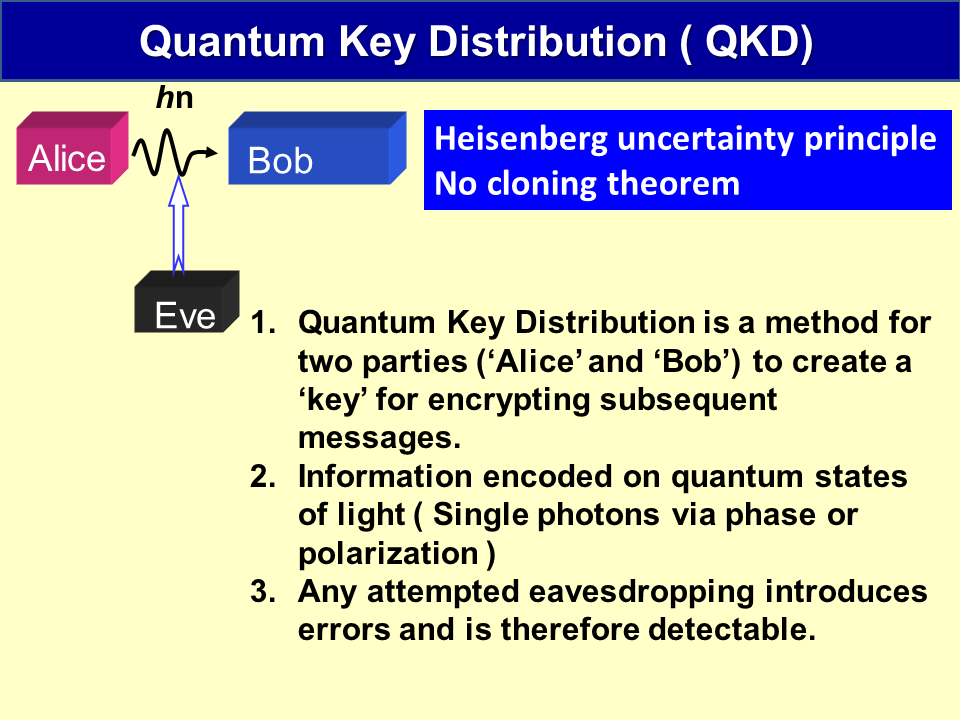
Welcome to the exciting frontier of Quantum Key Distribution (QKD) Technology—a course designed to take you deep into the world where physics and cybersecurity converge. As the digital world grows increasingly complex and vulnerable, classical cryptographic methods are being challenged by the looming power of quantum computing. QKD presents a revolutionary solution—leveraging the fundamental laws of quantum mechanics to create unbreakable encryption keys. This course will guide you through the fascinating landscape of QKD, from its scientific foundations to real-world systems deployed over fiber and satellite networks.
You’ll explore core quantum technologies, understand how QKD differs from traditional encryption, and examine the architecture of quantum cryptographic systems—from single-photon sources and detectors to protocol-level implementations like BB84 and E91. Real-world case studies and emerging applications such as secure communication for governments, banks, and defense agencies will be discussed, alongside cutting-edge advancements like satellite-based QKD and the roadmap toward the quantum internet. By the end of this course, you’ll not only understand how QKD works but also be equipped to critically analyze its market potential, limitations, and future role in global cybersecurity.
Course Content
Introduction
What are Quantum Technologies?
00:00Classical Cryptography
00:00Need for Quantum Key Cryptography?
00:00