The Future of Secure Computation: A Comprehensive Guide to Homomorphic Encryption
About Course
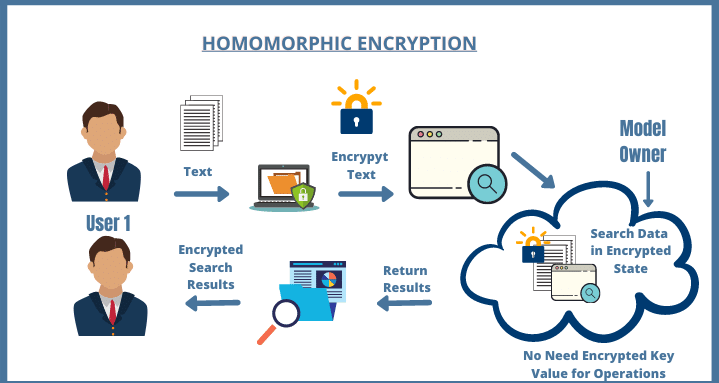
In today’s digital world, where privacy and data security are under constant threat, homomorphic encryption emerges as one of the most revolutionary concepts in cryptography. This course offers a deep dive into the future of secure computation, focusing on how homomorphic encryption allows data to be processed while still encrypted—eliminating the need to ever expose sensitive information. Through real-world examples, emerging use cases, and technical walkthroughs, learners will explore how this technology is reshaping sectors like cloud computing, AI, finance, healthcare, and national security.
Students will not only gain a strong theoretical foundation but also develop practical insight into the challenges and opportunities surrounding fully, partially, and somewhat homomorphic encryption. Whether you’re an aspiring cryptographer, a cybersecurity professional, or a policy strategist, this course equips you with the knowledge to understand and participate in the future of privacy-preserving computation.
Course Content
Introduction
Definition of homomorphic encryption
00:00Historical background and development
00:00Why homomorphic encryption is important
00:00