The Threat of 5G Cyberattacks: Securing the Next Generation of Networks
About Course
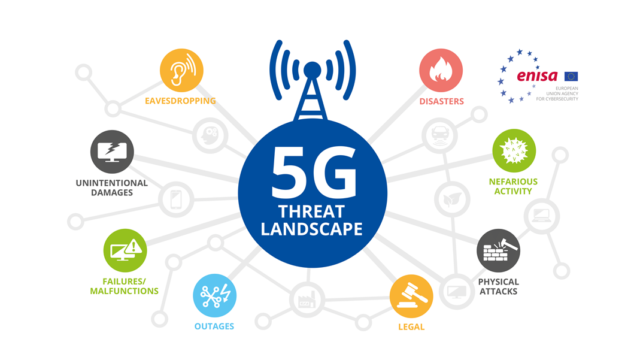
The rollout of 5G technology marks a transformative leap in global communication, promising lightning-fast speeds, ultra-low latency, and the capacity to connect billions of devices. However, as 5G powers everything from self-driving cars to smart cities and critical infrastructure, it also opens the door to unprecedented cybersecurity threats. In this course, you’ll explore the hidden dangers lurking within next-generation networks and gain a comprehensive understanding of how and why these systems are becoming prime targets for cyber attackers.
Through real-world case studies, technical breakdowns, and strategic solutions, students will learn how cybercriminals exploit the unique features of 5G infrastructure, including its decentralized nature and expanded attack surface. Whether you’re an IT student, cybersecurity enthusiast, or working professional, this course will arm you with the knowledge and tools to understand the evolving landscape of 5G threats—and how to defend against them. The future of digital connectivity is here, and it’s time to learn how to secure it.
Course Content
Introduction
What is 5G?
00:00Importance of 5G technology
00:00The potential for cyberattacks on 5G networks
00:00